Blooming.com.my is a local e-commerce site that selling flower and other small gifts such as cards bears, gourmet baskets and etc. They provide up to 100 pieces photos of hand bouquets and many other product listing. This will be convenient to customers for reviewing their products and easily understand the business of Blooming Florist. In contrast, customers who prefer touch n feel to products before purchase can visit Blooming Florist’s physical store which is located in LG level of Mid Valley.

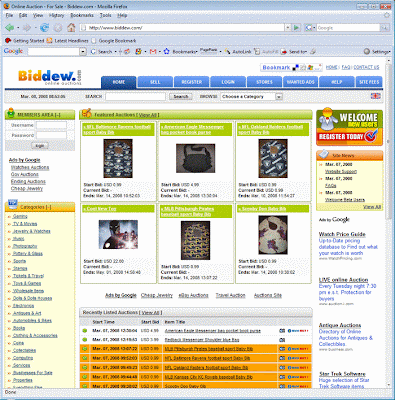
Homepage
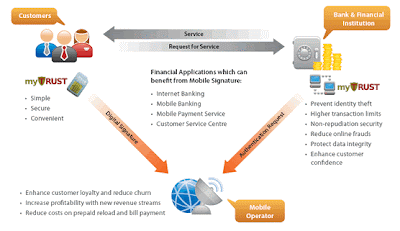
Similar to other e-commerce site, Blooming.com.my provide member registration and log in, shopping cart, search engine and so on. However, they provide some services that only members are able to read through, such as order tracking, gift reminder, address book and online payment.
Site navigation and paying method
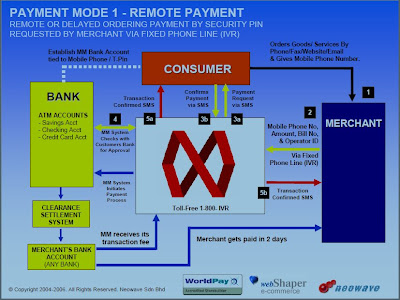
One of the fascinating point is Blomming.com.my not only provides delivery services to Selangor (where their physical store is located), but to all major towns area, including Sabah and Sarawak (with extra charge on certain area). Furthermore, they do accept online credit card payments, online banking and mobile payment.
Extra services and convenience screenshot
For consumer convenience purpose, Blooming.com.my has provided order tracking service where u can trace your order on the delivery status. In addition, live support is also provided so that customer could make enquiries on the spot, without wasting money to make a call. Many useful corners are also provided at the left hand site of the website like customer service corner, country selection for international delivery, info corner, “Tips corner”, and currency converter.
Conclusion and suggestion
In conclusion, although features in Blooming.com.my are simple, but it is enough for a basic internet user to deal with e-commerce. Basic internet user would not need too much or complicated steps in ordering and searching in the website. Nevertheless, Blooming.com.my has to make further improvement in their hand bouquets and also others product’s picture. Indeed, they are providing good services but the photos are not attractive enough. We believe after making this amendment, more visitor and customer will shop through Blooming.com.my for guarantee.


Homepage
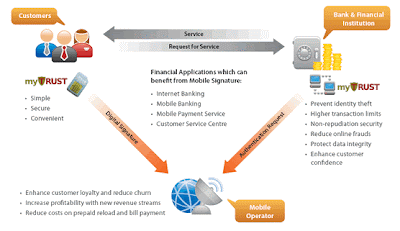
Similar to other e-commerce site, Blooming.com.my provide member registration and log in, shopping cart, search engine and so on. However, they provide some services that only members are able to read through, such as order tracking, gift reminder, address book and online payment.
Site navigation and paying method
One of the fascinating point is Blomming.com.my not only provides delivery services to Selangor (where their physical store is located), but to all major towns area, including Sabah and Sarawak (with extra charge on certain area). Furthermore, they do accept online credit card payments, online banking and mobile payment.
Extra services and convenience screenshot
For consumer convenience purpose, Blooming.com.my has provided order tracking service where u can trace your order on the delivery status. In addition, live support is also provided so that customer could make enquiries on the spot, without wasting money to make a call. Many useful corners are also provided at the left hand site of the website like customer service corner, country selection for international delivery, info corner, “Tips corner”, and currency converter.
Conclusion and suggestion
In conclusion, although features in Blooming.com.my are simple, but it is enough for a basic internet user to deal with e-commerce. Basic internet user would not need too much or complicated steps in ordering and searching in the website. Nevertheless, Blooming.com.my has to make further improvement in their hand bouquets and also others product’s picture. Indeed, they are providing good services but the photos are not attractive enough. We believe after making this amendment, more visitor and customer will shop through Blooming.com.my for guarantee.